Unique Bug Bounty Report Example
Bug bounty programs allow independent security researchers to report bugs to an organization and receive rewards or compensation.
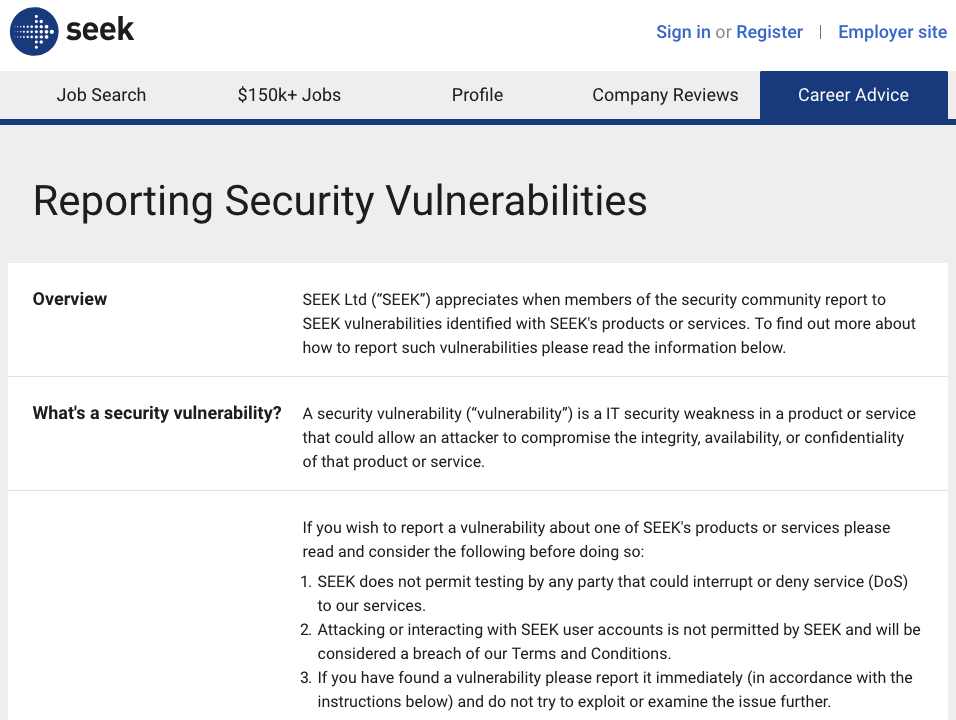
Bug bounty report example. A collection of templates for bug bounty reporting with guides on how to write and fill out. As I said in the intro the report is just as important as the pentest itself. Whose app are you downloading.
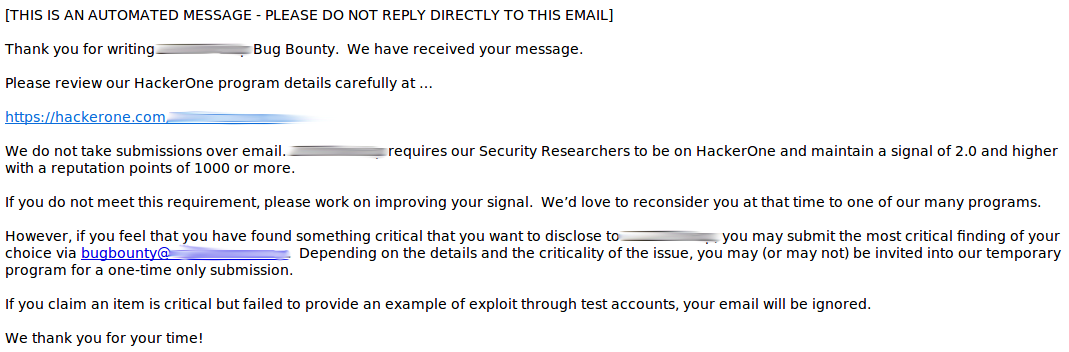
To learn more about how Intigriti can make running a bug bounty program a breeze schedule a demo with us today. Microsoft strives to address reported vulnerabilities as quickly as possible. Not the core standard on how to report but certainly a flow I follow personally which has been successful for me.
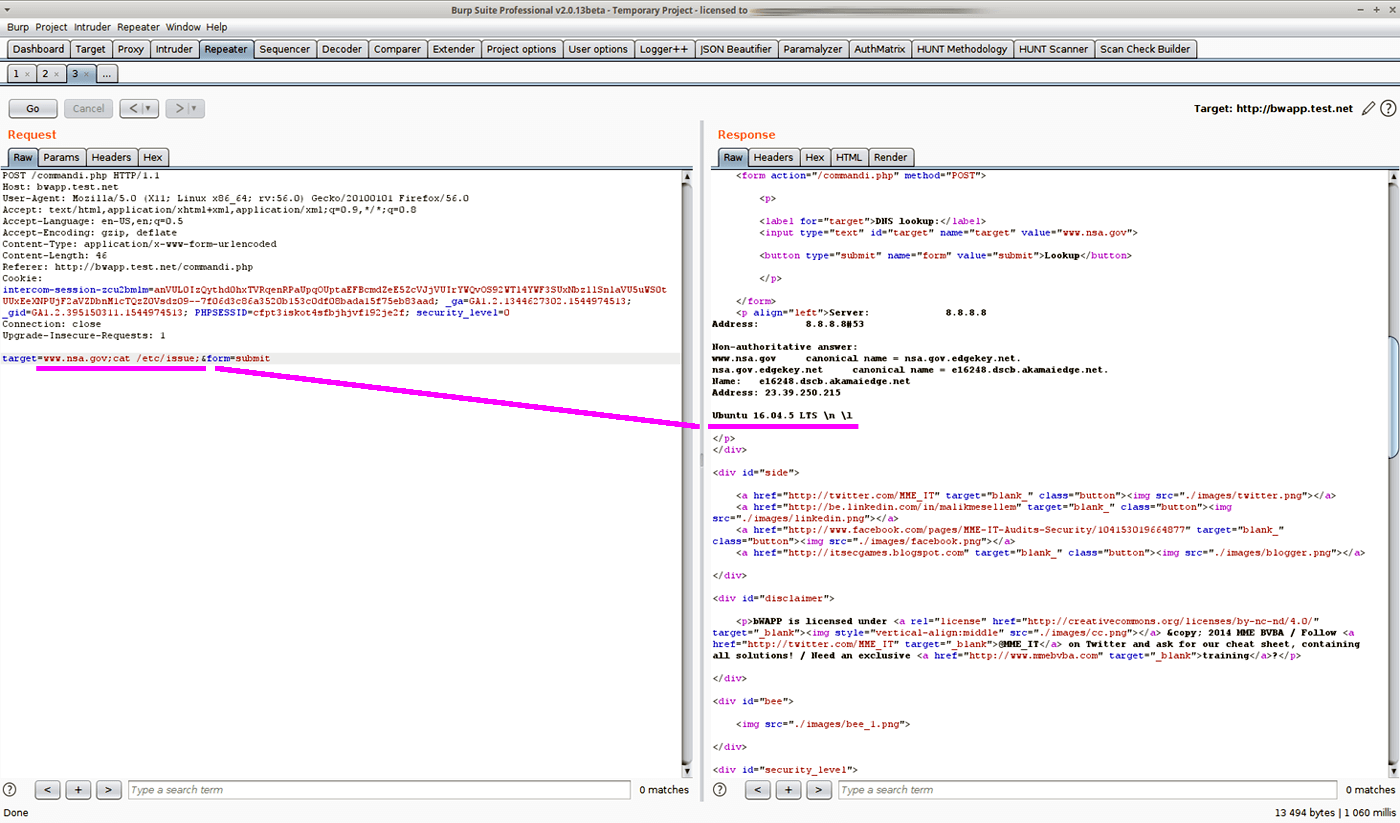
Actually the reason to it is due to the CNAME of the medavineco-DNS-entry. A sample report from hackerone. Here are some examples of publicly disclosed examples of good reports.
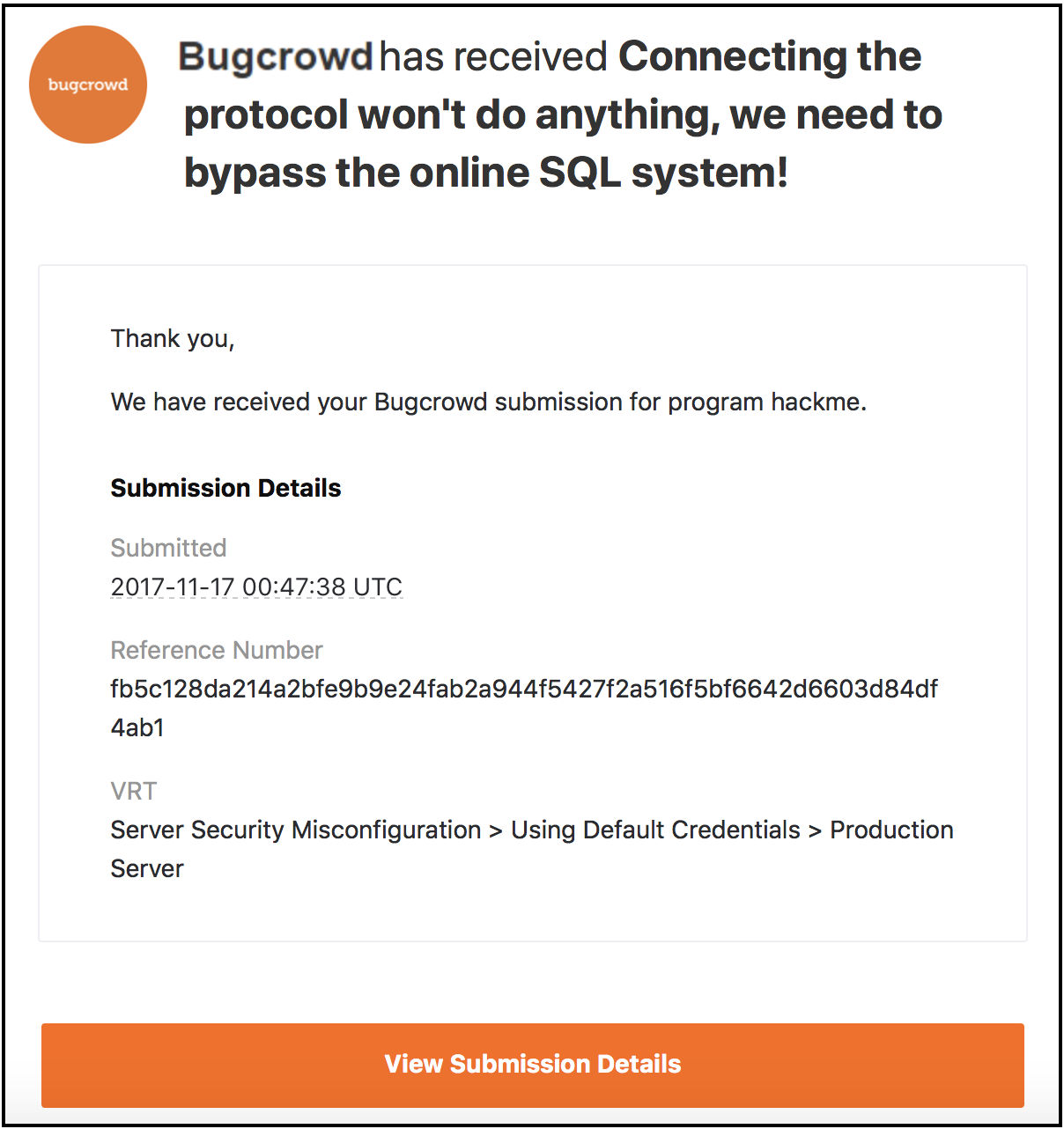
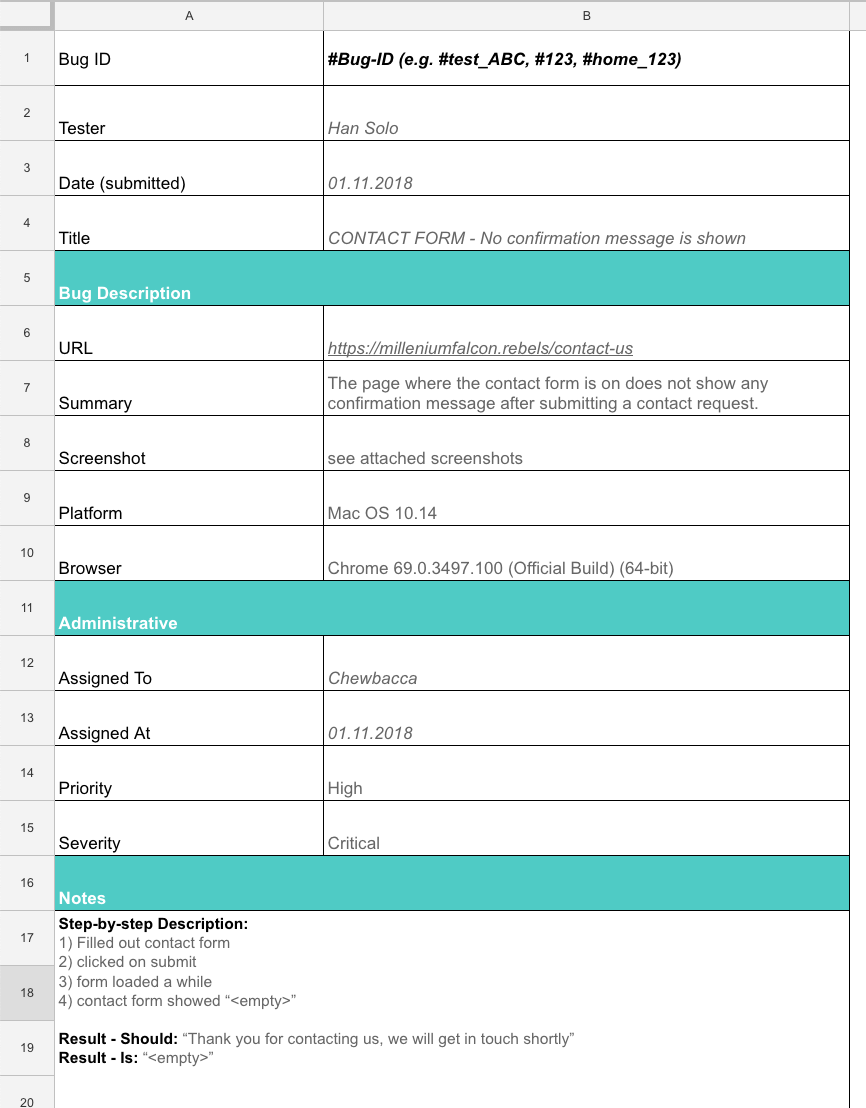
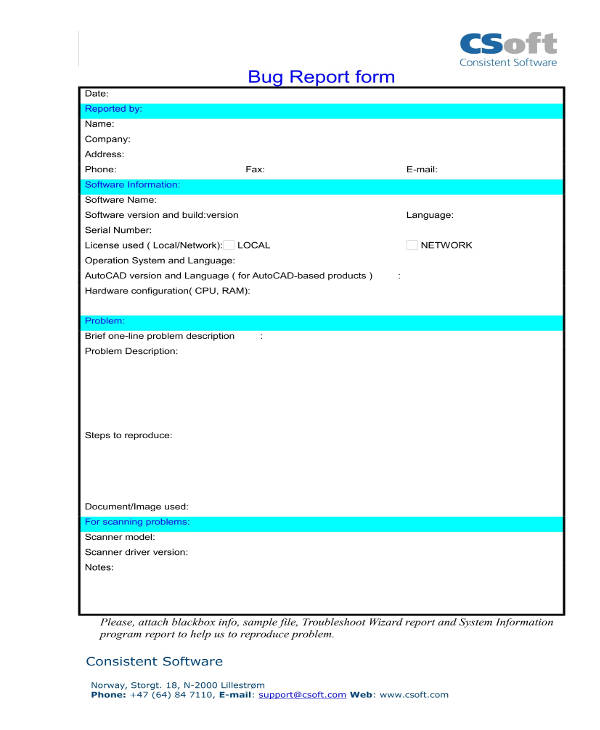
Todays is a guest post from Scott Robinson sd_robs on Twitter and SRobin on Bugcrowd. The Sample BugDefect Report given below will give you an exact idea of how to report a Bug in the Bug Tracking Tool. If you have any feedback please tweet us.
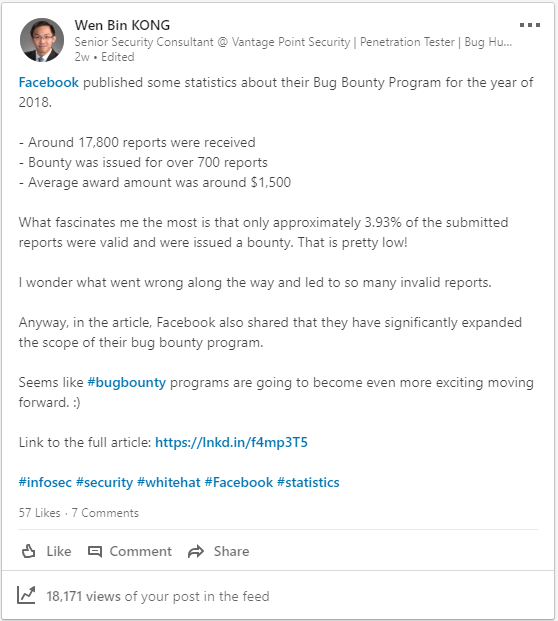
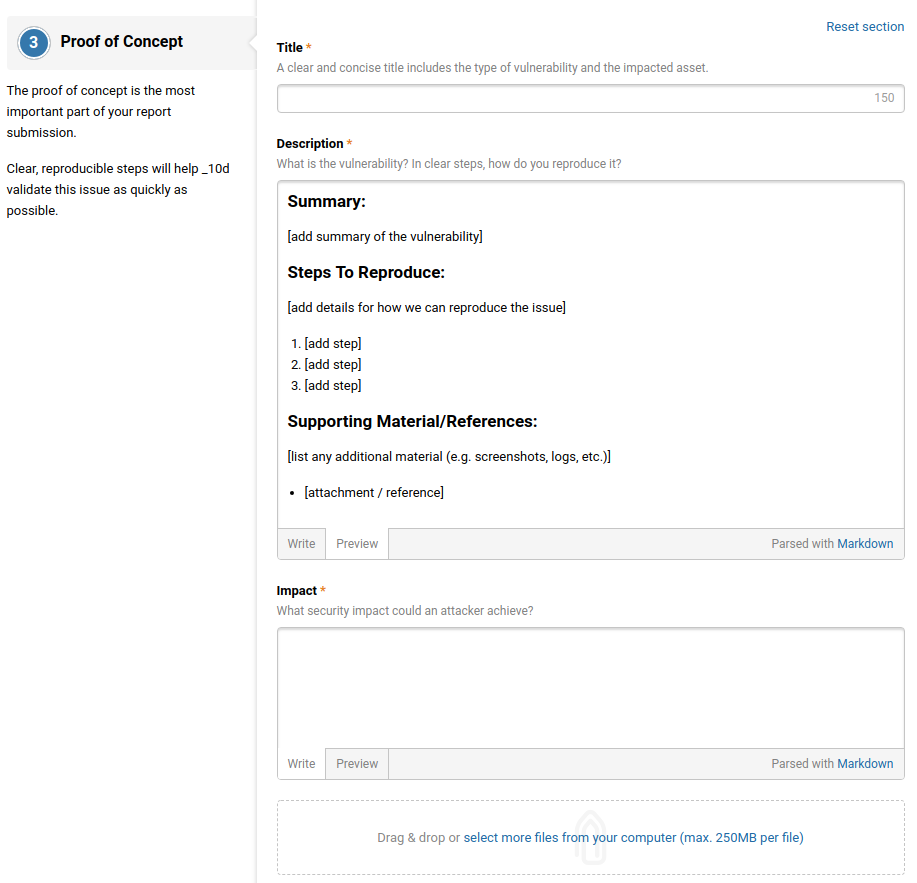
Critical Bug Bounty Reports. Good bug bounty reports speed up the triage process. OK jokes aside while writing reports is a very important part of bug bounty hunting we can simplify this whole process by following these basic guidelines.
Here is an Example scenario that caused a Bug. The most exhaustive list of known Bug Bounty Programs on the internet. Bug bounty platforms automate much of the process and a team of experts will deal with false-positive reports for you.